HacktheBox Binary Badlands 2024—Frontier Marketplace CTF Writeup
Welcome to another Capture-the-Flag (CTF) write-up! In this post, I’ll walk you through how I solved the FrontierMarketplace challenge in…
HTB CTF 2024 Binary Badlands: Blockchain-FrontierMarketplace
Welcome to another Capture-the-Flag (CTF) write-up! In this post, I’ll walk you through how I solved the FrontierMarketplace challenge in the Blockchain category. This challenge was part of HTB’s University CTF 2024, where our school proudly participated and secured the 120th spot on the leaderboard. Let’s dive into the solution and explore the steps I took to crack this challenge!
Description
In the lawless expanses of the Frontier Board, digital assets hold immense value and power. Among these assets, the FrontierNFTs are the most sought-after, representing unique and valuable items that can influence the balance of power within the cluster. This government has managed to win a lot of approval and consensus from the people, through a strong propaganda campaign through their FrontierNFT which is receiving a lot of demand. Your goal is to somehow disrupt the political ride of the Frontier Board party.
File Analyzation
Two endpoints are provided for interaction, one of which is accessible via netcat. This endpoint offers a simple interface, allowing us to retrieve the secret key, the marketplace contract address, and the setup contract address. Additionally, it enables us to reset the challenge and claim the flag once the challenge is solved.
First, we download the provided files! We’ve given 3 solidity files: FrontierMarketplace.sol FrontierNFT.sol Setup.sol

Let’s start analyzing the files!!
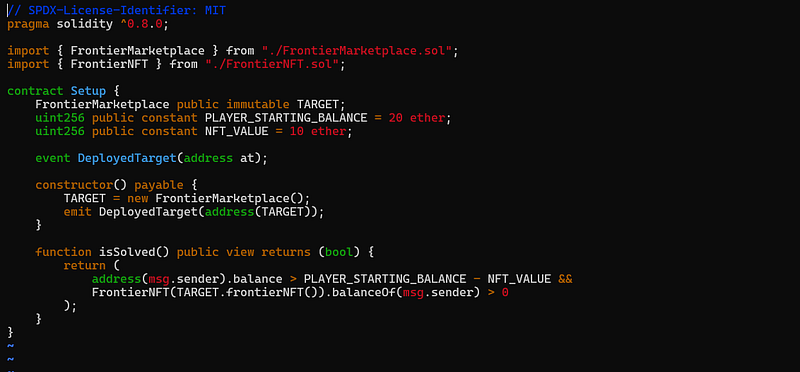
As shown here, this script defines the available balance and the price of the NFT. There’s also an isSolved function, which, based on my understanding, checks if we win by verifying if the combined total of our NFT balance and real balance exceeds 20 ether. Additionally, we need to own at least one NFT. Therefore, one possible way to win is by having a balance of 20 ether and one NFT.
How about the FrontierNTF.sol?
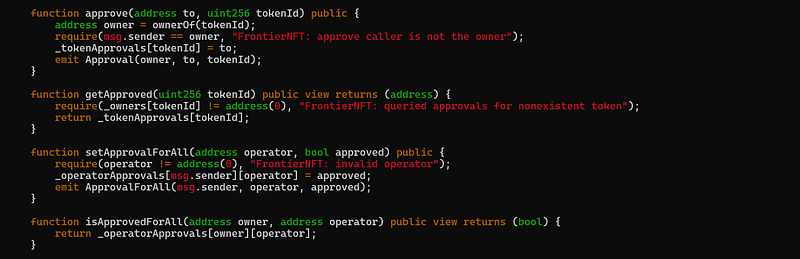
Both functions require the caller to be the token owner. However, the approvals are never cleared, meaning that once an address is approved for a token, it remains approved indefinitely. When purchasing a token, we can grant the marketplace approval for all tokens, allowing us to refund the token later. Alternatively, we can approve ourselves directly for the token, enabling us to transfer it to our own account whenever we choose.

This function ensures that the token can only be transferred by the owner, which is a positive aspect. However, it does not enforce that the owner must be the one to call the function. We just need to remember that the caller is the owner, approved for anyone, and for specific token.
By now, it should be clear how we can tackle the challenge. First, we purchase a token, then approve the marketplace for all tokens and give ourselves approval for the specific token. Afterward, we refund the token and retrieve it for ourselves.
Since the FrontierMarketplace.sol contract already exposes the frontierNFT contract, this becomes straightforward for us.
2. Exploitation
To exploit this, we’ll leverage Python, combining the power of ABI and web3. But before diving into the exploit, we need to first develop the ABI for the contracts involved. This will allow us to interact with the blockchain and the relevant contracts seamlessly, enabling us to perform the necessary actions like buying, approving, refunding, and transferring the NFT back to our account. Once the ABI is ready, we can proceed with the exploit and carry out the steps to manipulate the system to our advantage.
This is the ABI
To know your Private key, contract, setup, just use netcat and paste the IP to be able to access the simple interface of the challenge and type 1 (1 — Get connection informations).

Time for our exploit!!!
Run and we should have 1 NFT Balance

At this point, we can now access the interface again through netcat and get the flag!
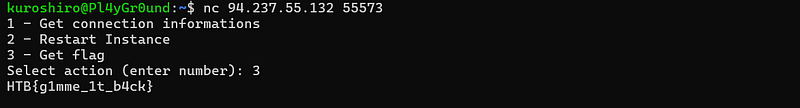
Conclusion
As a CTF participant with limited experience in blockchain hacking, I was thrilled to successfully solve this challenge through self-study. I took the time to dive into Solidity and gain a deeper understanding of how cryptocurrency operates at the programmatic level. This experience not only expanded my knowledge of smart contracts but also gave me a more practical perspective on the inner workings of decentralized applications. By learning how transactions, gas fees, and token approvals work, I was able to piece together the logic behind the exploit.
Last updated